Requirement: The function takes three inputs ProvisioningPlan, application name and the list entitlements that shouldn't be removed from the user. (This funtion can be used as a part of Mover workflow where a set of entitlements must not be removed from the user after provisioning due to mover event).
"Knowledge grows when you share". I would like to share my knowledge on Identity and Access Management.
Thursday, May 20, 2021
Code to update provisioning plan to remove the "Remove entitlement requests" from the provisioning plan
Monday, May 10, 2021
Quicklink to display the list of users who are expiring in next 14 days
Requirement: Develop a Quicklink, once we click on it, return the list of users who are expiring in next 14 days.
1. Create a quicklink category. Import the below file into Sailpoint to create quicklink category.
https://drive.google.com/file/d/1JzGYxpY_4BDZn2MZyKbRy22MNwt-hHN3/view?usp=sharing
2. Create a workflow quick link. Import the below file into Sailpoint to create quicklink.
https://drive.google.com/file/d/15_2GVWHXmHQcUQ44FYoeGGPKVUuJcBqm/view?usp=sharing
3. Create a workflow and add a form in it. Add a field in the form and add a rule for the field which returns the users who are expiring in next 14 days.
Import the below workflow into Sailpoint.
https://drive.google.com/file/d/13fdQcrH2HAiS44anmA0sLXB2Z-DZ5uX4/view?usp=sharing
Note: The rule is written with keeping below points in mind:
1. The user expiry is known from the Application attribute 'lastLogOn' of "HR System - Employees" application
2. The date format of 'lastLogOn' is in LDAP millisecond.
3. Convert the LDAP millisecond date to normal date and them compare it with current date. If the difference is <= 14 days, return the Identity Name.
Sunday, May 9, 2021
Email Template to send success message for Joiner
Sample Email template to send success message for Joiner. Download here:
https://drive.google.com/file/d/1Rgp3Pid_rWKRp9RxOsV8vysX6VX3ULtC/view?usp=sharing
Update the logo by convert the image to base64 encoded https://www.base64encode.org/ and replace in the email template.
Comment below if you find this post helpful.
Friday, May 7, 2021
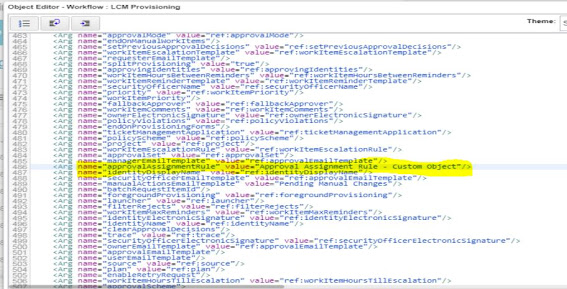
Defining Multi-level approval process
The approval assignment rule is written to trigger the approvals based on the approvers in the custom object.
Requirement:
If the user request for Entitlement to be added, for Active Directory the approvals has to go 3 approvers in serial manner.1. Manager
2. Security Admin (Work group)
3. IT Team (Work group)
For Account Request and Role Request, the approval has to go to manager.
Process:
Step 2: Import the Approval assignment rule into SailPoint. The Approval assignment rule contains the actual logic to trigger the approvals with the details from the custom object.
Step 3: Edit the LCM Provisioning Workflow and provide the name of imported assignment rule in argument approvalAssignmentRule for the sub processes Split provisioning and Approve and Provision.
step 4: Make sure approval mode = serial and approvalScheme = Identity.
Trigger a Life cycle event for Active Directory users who did not login for last 90 days
Go to setup --> Lifecycle Events --> Add New Lifecycle Event.
Enter the Name, Desription. Select Event type as Rule.
if(newIdentity!=null){
return true;
}else{
return false;
}
Or you can import the below IdentityTrigger Rule and use it.
import sailpoint.object.Identity;
import sailpoint.api.IdentityService;
import sailpoint.object.Link;
import sailpoint.object.Attributes;
import sailpoint.object.Application;
import java.util.Calendar;
import java.util.Date;
import java.text.SimpleDateFormat;
log.error("Identity Selector Rule Triggered : " + identity.getName());
// get the application link for Active Directory
IdentityService identityService = new IdentityService(context);
Application app = context.getObjectByName(Application.class, "HR System - Employees");
List links = identityService.getLinks(identity, app);
if(!links.isEmpty()){
Link link = links.get(0);
if(link!=null){
String applicationName = link.getApplicationName();
log.error("Application Name: " + applicationName);
Attributes attributes = link.getAttributes();
if(attributes!=null){
String lastLogOn = attributes.getString("lastLogOn");
String userAccountControl = attributes.getString("userAccountControl");
if(lastLogOn != null && userAccountControl != null) {
// convert from millisecond to date format
Date currentDate=new Date();
Long diffForDateAndTime = 11644473600000L;
Long adDate = Long.parseLong(lastLogOn);
Long epochTime = (adDate / 10000) - diffForDateAndTime;
Date lastLogOnDate = new Date (epochTime);
log.error("lastLogOnDate: " + lastLogOnDate);
//calucalate the diff b/w today to lastLogOn date
int diffInDays = (int) ((currentDate.getTime() - lastLogOnDate.getTime()) / (1000*60*60*24));
log.error("diffInDays: " + diffInDays);
//Event generation condition
if(diffInDays>90 && userAccountControl.equalsIgnoreCase("514")){
// log.error("************** Returning True *******************");
return true;
}
}
}
}
}
return false;
Run the refresh identity cube task with Process Events enabled. You can see the events are generated for the users that are inactive and not login into AD for last 90 days.
Thursday, May 6, 2021
Remove Identity Entitlements for any application
Field Value Rule to remove identity entitlements for any application
In a given application, call this rule in the Provisioning Policy entitlement field, to remove the entitlements. Below is the rule:
import sailpoint.object.EntitlementGroup;
import sailpoint.object.Attributes;
import sailpoint.object.ProvisioningPlan;
import sailpoint.object.ProvisioningPlan.AccountRequest;
import sailpoint.object.ProvisioningPlan.AttributeRequest;
import sailpoint.api.Provisioner;
log.error("Executing Feild Value Rule - Remove Entitlements for Identity: " + identity.getName());
String applicationName = link.getApplicationName();
String nativeIdentity = link.getNativeIdentity();
ProvisioningPlan plan = new ProvisioningPlan();
Provisioner provisioner = new Provisioner(context);
//Calucalting Identity Entitlements
List exceptions = identity.getExceptions();
if(exceptions !=null){
for(EntitlementGroup entitlement: exceptions){
Attributes attributes = entitlement.getAttributes();
Map attributesMap = attributes.getMap();
for (Map.Entry attrMap : attributesMap.entrySet()){
ProvisioningPlan.AccountRequest accountRequest = new ProvisioningPlan.AccountRequest(
ProvisioningPlan.AccountRequest.Operation.Modify, applicationName, null, nativeIdentity);
ProvisioningPlan.AttributeRequest attributeRequest = new ProvisioningPlan.AttributeRequest(
(String) attrMap.getKey(), ProvisioningPlan.Operation.Remove, attrMap.getValue());
accountRequest.add(attributeRequest);
plan.add(accountRequest);
provisioner.execute(plan);
}
}
}
Identity Creation Rule to generate username and full name
Identity Creation Rule to generate username and full name based on given conditions.
Username condition:1. First letter of first name + last name
2. First letter of first name.last name
3. first name.last name
4. last name.first letter of first name
5. last name.first name
6. If middele name exists: first letter of first name.first letter of middle name + last name
7. Generate a random integer and append to "newuser"
If the username genereated based on first condition already exists, then go to second condition. If second condition also exists, then go to third condition and so on.
Full name condition:
fullName = firstName + lastName + fatherName + grandFatherName;
Below is the code for Identity Creation Rule:
import sailpoint.object.QueryOptions;
import sailpoint.object.Filter;
import sailpoint.object.Identity;
import sailpoint.services.custom.utility.CustomUtil;
String firstName = account.getStringAttribute("firstName");
String lastName = account.getStringAttribute("lastName");
String middleName = account.getStringAttribute("middleName");
String fatherName = account.getStringAttribute("fatherName");
String grandFatherName = account.getStringAttribute("grandFatherName");
String [] userNameFullName = CustomUtil.getFinalUserNameFullName(firstName, middleName, lastName, fatherName, grandFatherName, context);
Logger log = Logger.getLogger("Custom.Rules.Custom-IdenitityCreation-HRMS");
log.setLevel(Level.DEBUG);
log.debug("firstName: "+firstName);
log.debug("lastName: "+lastName);
log.debug("middleName: " +middleName );
log.debug("fatherName: " +fatherName );
log.debug("grandFatherName: " +grandFatherName );
log.debug("username: "+ userNameFullName[0]);
log.debug("fullname: "+ userNameFullName[1]);
identity.setAttribute("username", userNameFullName[0]);
identity.setAttribute("fullname", userNameFullName[1]);
}
Below is the CustomUtil.java class, which has to be deployed:
package sailpoint.services.custom.utility;
import sailpoint.object.QueryOptions;
import sailpoint.object.Filter;
import sailpoint.object.Identity;
import java.util.ArrayList;
import java.util.Arrays;
import java.util.List;
import java.util.Random;
import sailpoint.api.SailPointContext;
import org.apache.log4j.Logger;
import org.apache.log4j.Level;
public class CustomUtil {
public String checkUserName(String username, SailPointContext context) throws Exception{
Logger log = Logger.getLogger("Custom.Rules.CustomUtil.checkUserName");
log.setLevel(Level.DEBUG);
QueryOptions identityQuery = new QueryOptions();
identityQuery.addFilter(Filter.eq("username", username));
List<Identity> identityList = context.getObjects(Identity.class,identityQuery);
if (!identityList.isEmpty()){
log.error("username already exist for identity: " + identityList);
return "TRUE";
}else{
return "FALSE";
}
}
public String[] getUserNameFullName(String firstName, String middleName, String lastName, String fatherName, String grandFatherName, SailPointContext context) throws Exception{
String [] userNameFullName = {"", ""};
userNameFullName[0] = getUserName(firstName, middleName, lastName, context);
userNameFullName[1] = getFullName(firstName, lastName, fatherName, grandFatherName);
return userNameFullName;
}
public String getUserName(String firstName, String middleName, String lastName, SailPointContext context) throws Exception{
Logger log = Logger.getLogger("Custom.Rules.CustomUtil.getUserName");
log.setLevel(Level.DEBUG);
String userName = null;
if(firstName!=null && !firstName.isEmpty() && lastName !=null && !lastName.isEmpty()) {
//First Condition
userName = firstName.charAt(0) + lastName;
log.debug("First Condition userName: "+userName);
if(checkUserName(userName, context).equalsIgnoreCase("TRUE")){
//Second Condition
userName = firstName.charAt(0) + "." + lastName;
log.debug("Second Condition userName: "+userName);
}else{
return userName;
}
if(checkUserName(userName, context).equalsIgnoreCase("TRUE")){
//Third Condition
userName = firstName + "." + lastName;
log.debug("Third Condition userName: "+userName);
}else{
return userName;
}
if(checkUserName(userName, context).equalsIgnoreCase("TRUE")){
//Fourth Condition
userName = lastName + "." + firstName.charAt(0);
log.debug("Fourth Condition userName: "+userName);
}else{
return userName;
}
if(checkUserName(userName, context).equalsIgnoreCase("TRUE")){
//Fifth Condition
userName = lastName + "." + firstName;
log.debug("Fifth Condition userName: "+userName);
}else{
return userName;
}
if(checkUserName(userName, context).equalsIgnoreCase("FALSE")){
return userName;
}
// Final condition - if middlename exists
if(checkUserName(userName, context).equalsIgnoreCase("FALSE") && !middleName.isEmpty()){
//Sixth Condition
userName = firstName.charAt(0) + "." + middleName.charAt(0) + lastName;
log.debug("Sixth Condition userName: "+userName);
return userName;
}
}
//Final condition - generate random integer and append it to first condition
Random rand = new Random();
int rand_int = rand.nextInt(1000);
String rand_str = String.valueOf(rand_int);
userName = "newuser" + rand_str;
return userName;
}
public String getFullName(String firstName, String lastName, String fatherName, String grandFatherName){
String fullName = firstName + " "+ lastName + " " + fatherName + " " + grandFatherName;
return fullName;
}
public String[] getFinalUserNameFullName(String firstName, String middleName, String lastName, String fatherName, String grandFatherName, SailPointContext context) throws Exception{
String [] userNameFullName = getUserNameFullName(firstName, middleName, lastName, fatherName, grandFatherName, context);
return userNameFullName;
}
}
Form AllowedValues rule to filter Identities with Active Regular Active Directory accounts and identity is active and correlated
The rule type is AllowedValues. import org.apache.log4j.Level ; import org.apache.log4j.Logger ; import sailpoint.object.Filter ; import sa...
-
Beanshell script to display all the entitlements assigned to an identity: import java.util.List; import java.util.Iterator; import sailpoin...
-
This post provides you the information about various SailPoint IIQ installation topologies. Please refer to SailPoint IIQ support matrix for...
-
This post provides the steps to install Sailpoint IdentityIQ 7.3 for a micro footprint installation topology. Please check the SailPoint II...